Here's why you can't trust a text message
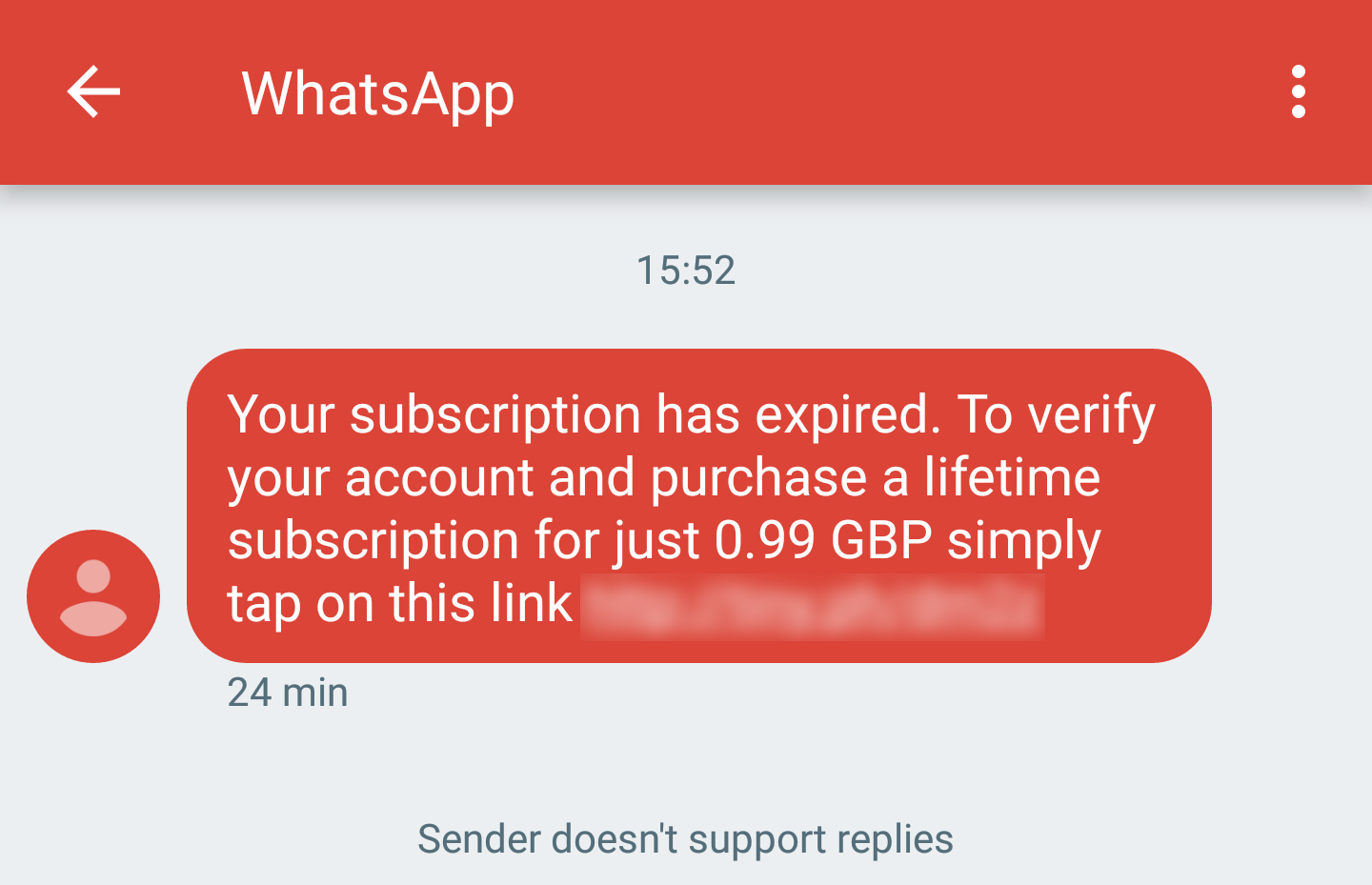
Last weekend, I received a notification by text that my WhatsApp subscription had expired. Immediately recognising this as a scam, I decided to investigate further.
I began by opening the full conversation in my messaging app, so that I could see any extra details which might help. The sender was labelled as "WhatsApp", which confused me, because I hadn't had a text from WhatsApp before and this definitely wasn't a message from the company.
It turns out that instead of a phone number, an alphanumeric sender ID can be used as the value of the "TP-OA" field. It's this field that your phone uses to display the sender, and it can be set by anyone at will, making exploiting a user's trust in their messaging app surprisingly easy. In some countries, a sender ID must be verified by the SMS carrier first. In the UK, however, there are no restrictions other than that the value must be alphanumeric and cannot exceed a length of 11 characters.
Confident that no more trickery was going on in the text message, I next decided to work out what the scammers were aiming for. Of course, they made the next steps nice and clear to the user. All I had to do was click a short link which would take me to the page needed to 'renew my subscription'.
I didn't want to click the link immediately, but I was curious at to where it would lead. Running the 'curl' command on my machine quickly revealed that a URL shortening service had been used, Tiny Url to be specific. They offer public APIs for every hash, and so I was able to use this to determine the destination of this link as well as the number of times that it had been clicked:
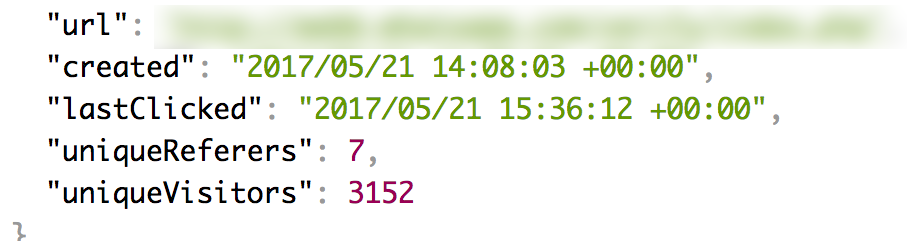
It had only been created around an hour ago, and over 3000 unique visitors had been tracked, and so this text was definitely being sent on a fairly large scale. With the hash being so new, my guess is that some software has been created to generate new URLs and domains periodically so that the scam can continue.
The next step in my investigation was to take a look at the website itself. Other than the appalling design and a broken footer, there wasn't much to see, and so I went straight to the source code. Unfortunately, rather than seeing an inspirational use of the latest web platform features, I was greeted by some ugly JavaScript and a giant variable full of gibberish:
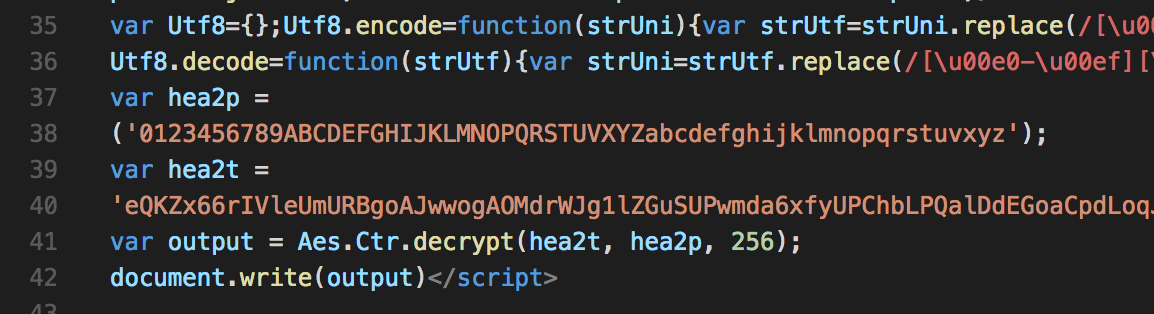
It turns out that the page was rendered by using AES decryption and a basic cipher to bring the source into memory, at which point it is dumped out onto the page. There wasn't much to hide, leaving me to guess that this was just a way of tricking abuse prevention tools. In fact, a StackOverflow search for ways of hiding a page's source code led me straight to a GitHub Gist containing the script being used. Bingo!
The site itself exists simply to harvest billing credentials. A PHP script (running over HTTP, of course) collected the needed information using a basic form. I never used my real details, for obvious reasons, but did follow through the whole procedure. A few POST requests later, and I was redirected to the actual WhatsApp website. The scam was complete!
To put all of this into context, here is a timeline of events:
- 21/05/17: Four domains registered using the WHOIS details I found. Two referenced WhatsApp and one impersonated the DVLA (a Government agency in the UK). I was sadly unable to identify the fourth.
- 21/05/17: Text message received. Shortened URL had been up for around an hour.
- 21/05/17: Attempted to contact DNS and web server host.
- 21/05/17: Google Chrome begins warning users that the site is deceptive, and deters users from accessing it. I had no involvement with this - presumably automated/based on user reports?
- 22/05/17: Initial contact made with owner of Tiny Url site. Link disabled and Darian tells me that similar URLs have been spotted before.
- 26/05/17: Domain suspended by registrar.
- 28/05/17: Blog post published. No further activity spotted, although changing domain name and registration details would be fairly easy for the scammer.
To wrap all of this up, I just want to thank Darian from Tiny Url who was extremely helpful in putting a stop to this. To do the responsible thing, I want to point out that both WhatsApp and Tiny Url are genuinely useful services. It's a shame that they have been abused for this purpose, but I wouldn't want for it to cause them any damage.